Security Awareness Training That Actually Sticks!
Hands-on exercises that build real cybersecurity skills through practice, not passive watching.
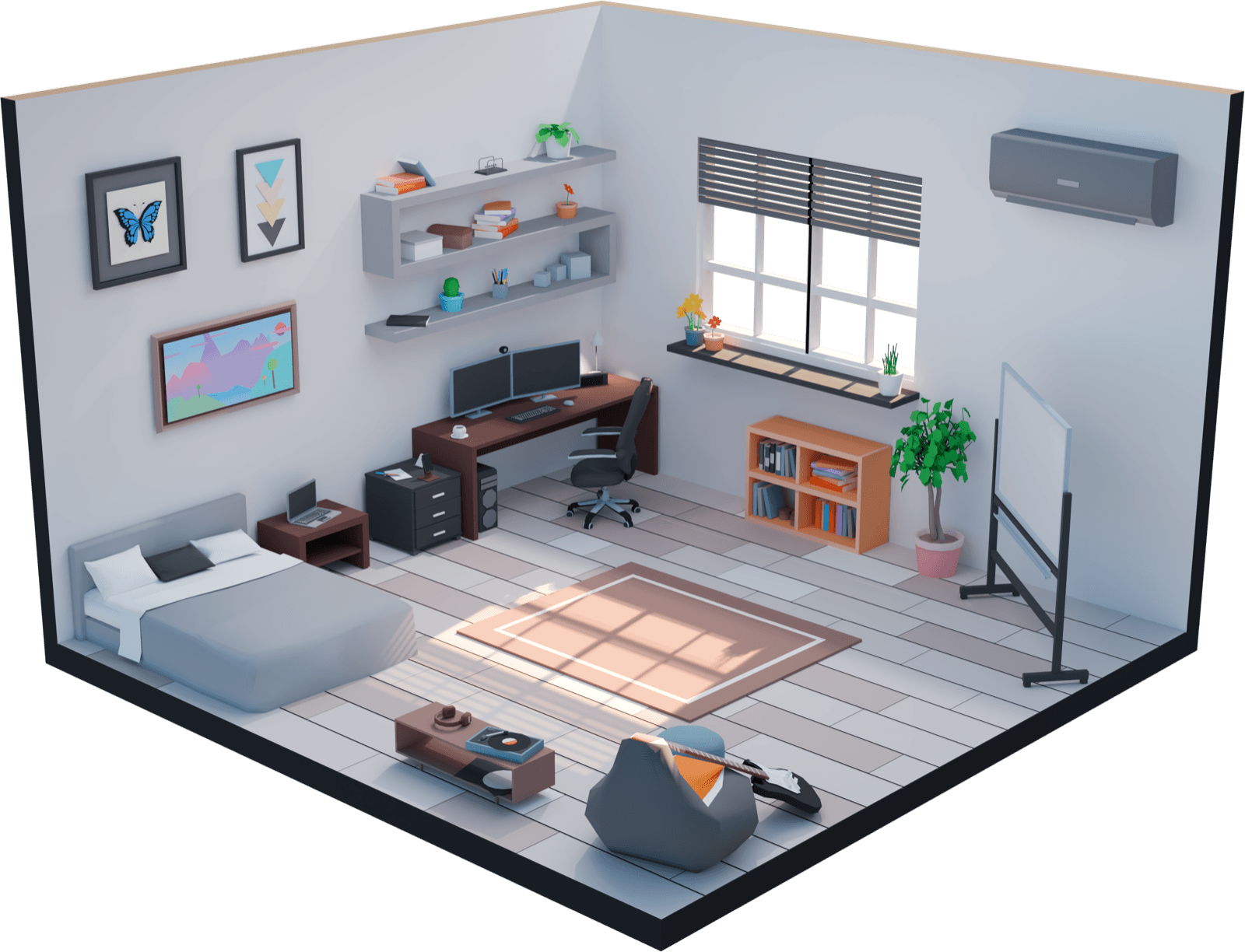
See RansomLeak in Action
Watch how our interactive 3D platform transforms security awareness training into an engaging, memorable experience.
Exercise Library
No sign-up required — start learning immediately.
Security Awareness Exercises
Master the fundamentals of cybersecurity with exercises covering the most common attack vectors and threats.

Phishing
Recognize and identify the features of a phishing message and website. Understand the consequences of falling for a phishing attack and how to mitigate its impact using official reporting channels.

Ransomware
Your goal is to learn how to identify malicious programs, particularly those delivered via phishing emails, and understand the steps to take if you suspect a ransomware attack.
Social Engineering
Recognize manipulation tactics during phone calls. Practice verification techniques when strangers request sensitive information or attempt to gain unauthorized access to restricted areas.
Social Media Oversharing
Learn how seemingly harmless social media interactions can inadvertently provide attackers with crucial intelligence needed to craft highly targeted and convincing social engineering attacks.
Vishing
Identify voice-based phishing attacks during phone calls and practice verification techniques. Understand how attackers use urgency and authority to manipulate victims.
Data Leakage
Recognize how sensitive information can be accidentally exposed through email, file sharing, and improper document handling. Practice data classification and secure information management.
Smishing
Simulate falling victim to a text-based phishing attack and learn prevention strategies to protect yourself and your organization.
Double Barrel Phishing
Learn the common tactics and red flags related to double barrel phishing attacks that combine multiple deception techniques.
Business Email Compromise
Identify fraudulent executive emails requesting urgent financial transactions. Practice verification procedures before processing any sensitive requests.
Whaling With A Deepfake
Understand how senior executives can be compromised through targeted whaling attacks. Learn what deepfakes are and how they facilitate fraud.
Learn from Real-World Incidents
Study actual security breaches that made headlines and understand how to prevent similar incidents in your organization.
OneNote Email Attack
Experience a sophisticated phishing attack reported by a Reddit user where attackers compromise an external client`s email, monitor correspondence, then register a lookalike domain to impersonate the client.
MGM Resorts Breach
Discover how a simple phone call led to a major breach at one of the world's largest hotel chains. This module breaks down how attackers used social engineering to impersonate an employee, gain helpdesk access, and compromise critical systems.
Platform Features
Everything you need to build a strong security culture in your organization
Enterprise-Grade Analytics Dashboard
Gain comprehensive visibility into your organization's security posture with real-time analytics. Track completion rates, identify risk areas, and measure training effectiveness across departments with executive-level reporting capabilities.
Seamless SCORM Integration
Deploy enterprise security training instantly with full SCORM 1.2 and 2004 compliance. Integrate seamlessly with your existing LMS infrastructure –the no custom development or IT overhead required.
Dedicated Multi-Tenant Architecture
Secure, isolated tenant environments ensure complete data segregation and customization. White-label the platform with your branding, configure role-based access controls, and maintain enterprise-grade security compliance.
Why RansomLeak?
Security awareness training that's accessible, engaging, and effective for everyone.
Learn by Doing
Practice recognizing threats and making smart decisions in simulated real-world situations.
Actually Engaging
No boring slides or dry videos. Our gamified approach keeps you focused, alert, and genuinely interested from start to finish.
Comprehensive Topics
Explore a wide range of security awareness topics from password protection to advanced threat detection, tailored to both beginners and experts.
Made by Industry Veterans
Built by seasoned cybersecurity professionals with decades of real-world experience protecting organizations from evolving threats.
Frequently Asked Questions
Everything you need to know about deploying enterprise security awareness training
Still have questions? Our team is here to help.
Chat With Us